Organization Settings¶
The Organization Settings page is your central hub for managing security, API access, and audit logging. Configure your organization details, manage API tokens, set up trusted IP addresses, and monitor security events.
Overview¶
Organization Settings provides:
- Organization Details - Basic information and timezone configuration
- API Token Management - Create and manage authentication tokens
- Trusted IP Security - IP-based access control with CIDR support
- IP Audit Logs - Comprehensive security event monitoring
- User Management - Control access and permissions
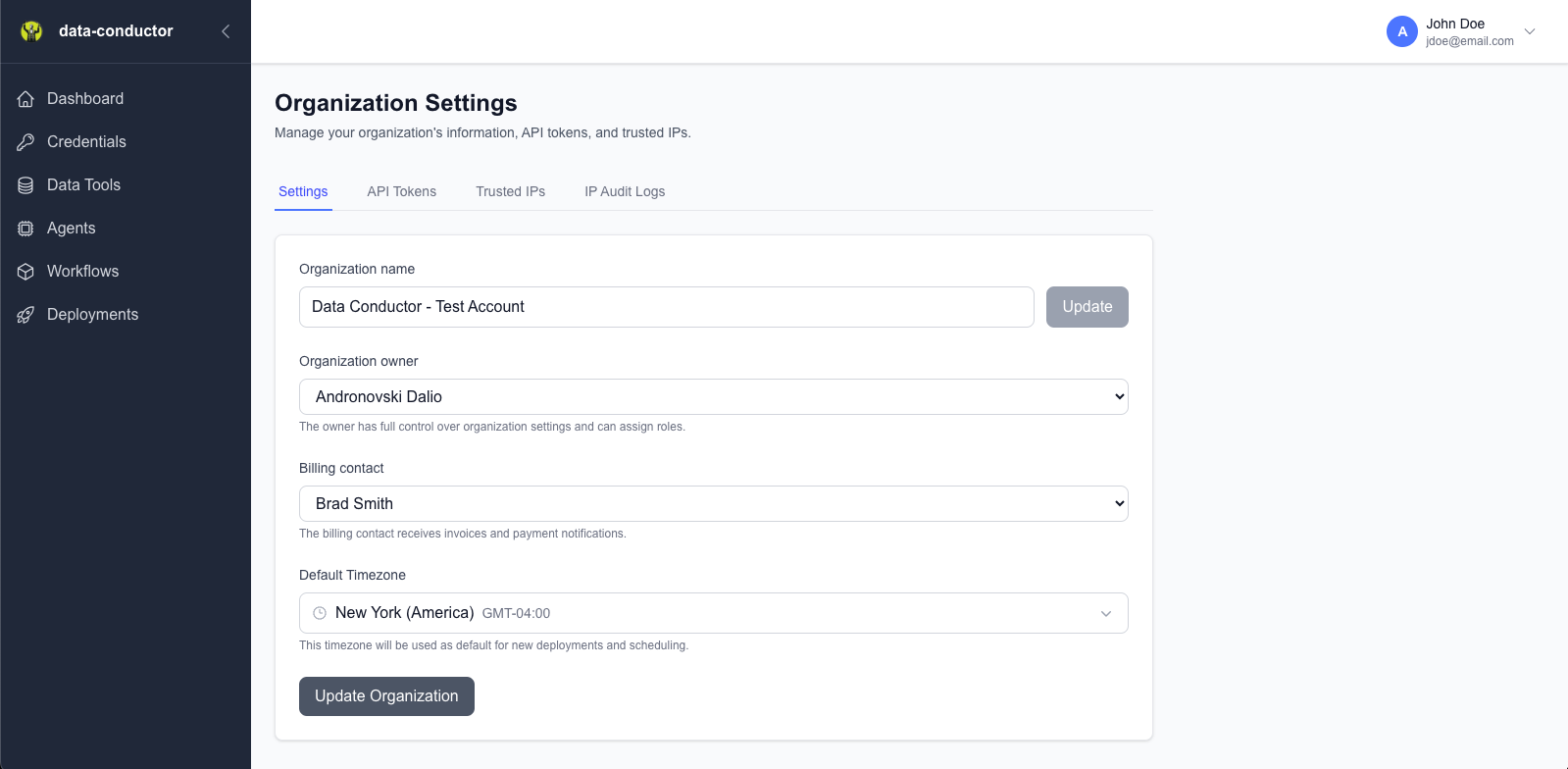 Main organization settings with tabbed interface
Main organization settings with tabbed interface
Organization Details¶
Basic Information¶
Configure your organization's core details:
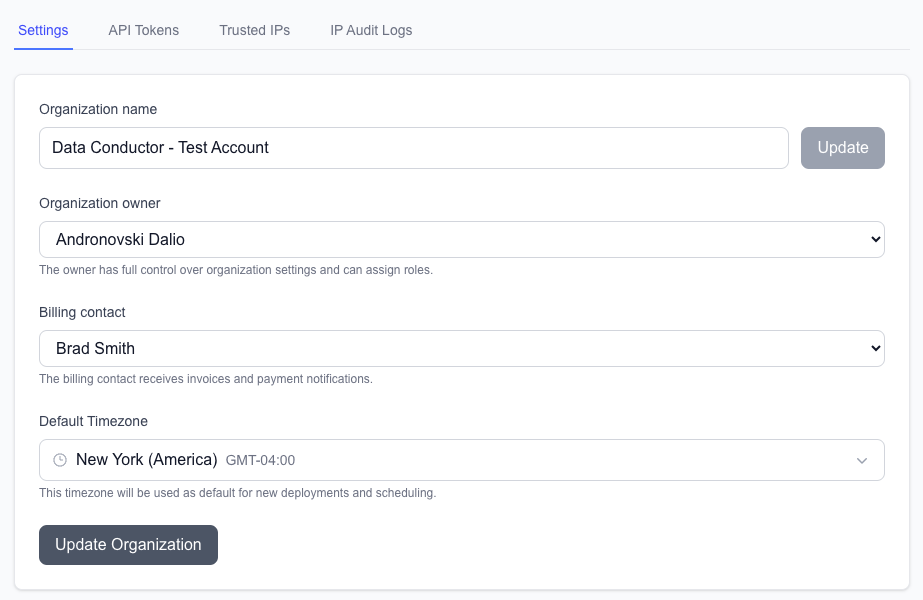 Organization information configuration
Organization information configuration
Required Fields: - Organization Name: Your company or team name - Description: Purpose and context for the organization - Timezone: Used for CRON scheduling and audit logs
Configuration Example:
Organization Name: Acme Data Analytics
Description: Data processing and analytics for Acme Corporation
Timezone: America/New_York
Timezone Configuration¶
The organization timezone affects: - CRON Scheduling: All deployment schedules use this timezone - Audit Logs: Timestamps displayed in organization timezone - User Interface: Date/time displays throughout the platform
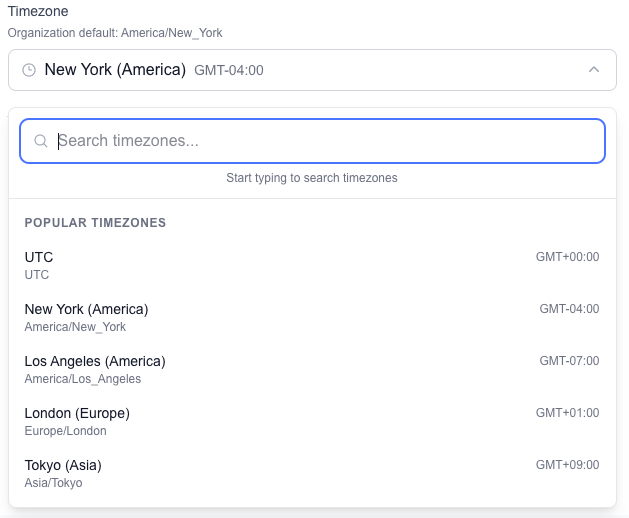 Timezone selector with search functionality
Timezone selector with search functionality
Supported Timezones: - All standard IANA timezone identifiers - Automatic daylight saving time handling - Real-time preview of current time in selected zone
API Token Management¶
Creating API Tokens¶
API tokens authenticate external systems and API deployments:
Step-by-step API token creation process
Token Creation Process: 1. Navigate to API Tokens tab 2. Click Create New Token 3. Provide token details: - Name: Descriptive identifier - Description: Purpose and usage notes - Permissions: Access level (if applicable) 4. Save and securely store the token
 API token creation dialog with security notes
API token creation dialog with security notes
Token Management¶
Token Information Displayed: - Name & Description: Token identification - Created Date: When token was generated - Last Used: Most recent authentication (if available) - Status: Active/Inactive state
 Active API tokens with management options
Active API tokens with management options
Token Security¶
Security Best Practices: - Store tokens securely (password managers, environment variables) - Rotate tokens regularly (recommended: every 90 days) - Use different tokens for different applications - Monitor token usage in audit logs - Immediately revoke compromised tokens
Token Usage:
# Example API request with token
curl -H "Authorization: Bearer your-api-token-here" \
-H "Content-Type: application/json" \
https://your-data-conductor-instance.com/api/endpoint
Trusted IP Addresses¶
IP-Based Security¶
Control access to your data-conductor instance using IP address filtering:
Configuring trusted IP addresses and CIDR ranges
Supported IP Formats:
- Single IPv4: 192.168.1.100
- IPv4 CIDR: 192.168.1.0/24
- Single IPv6: 2001:db8::1
- IPv6 CIDR: 2001:db8::/32
Adding Trusted IPs¶
 Adding new trusted IP addresses
Adding new trusted IP addresses
Configuration Fields: - IP Address/Range: IP or CIDR notation - Description: Purpose and context - Active: Enable/disable without deletion
Common Use Cases:
Office Network: 203.0.113.0/24
VPN Gateway: 198.51.100.50
Home Office: 192.0.2.100
Cloud Service: 203.0.113.200/29
IP Validation Logic¶
Access Control Flow: 1. User attempts to access data-conductor 2. System extracts client IP address 3. IP is checked against trusted IP list 4. Access granted if IP matches any trusted entry 5. Access denied and logged if no match found
 IP address validation and access control process
IP address validation and access control process
Advanced IP Features¶
CIDR Range Support: - Specify IP ranges using CIDR notation - Supports both IPv4 and IPv6 - Automatic subnet calculations - Wildcard and range validations
IPv6 Support: - Full IPv6 address support - Compressed notation handling - Mixed IPv4/IPv6 environments - Future-proof network configurations
IP Audit Logs¶
Security Event Monitoring¶
Track all IP-related security events:
Reviewing security events and access attempts
Logged Events: - Successful Access: Trusted IP authentication - Blocked Access: Untrusted IP access attempts - IP Configuration Changes: Trusted IP list modifications - Token Usage: API token authentication events
 Comprehensive audit log with filtering options
Comprehensive audit log with filtering options
Log Information¶
Each Audit Entry Contains: - Timestamp: When event occurred (organization timezone) - Event Type: Success, failure, configuration change - IP Address: Source IP of the request - User Agent: Browser/client information - Action: Specific action attempted - Result: Success/failure with details
Filtering and Search¶
Available Filters: - Date Range: Specific time periods - Event Type: Success/failure/configuration - IP Address: Specific IPs or ranges - User: Specific user accounts
 Filtering options for audit log analysis
Filtering options for audit log analysis
Security Analysis¶
Use Audit Logs For: - Security Monitoring: Detect unauthorized access attempts - Compliance: Maintain access records for audits - Troubleshooting: Identify IP configuration issues - Pattern Analysis: Monitor usage patterns and anomalies
Common Patterns to Monitor:
Repeated Failed Attempts: Potential brute force attacks
New IP Addresses: Unexpected access sources
Geographic Anomalies: Access from unusual locations
Time-based Patterns: Off-hours access attempts
User Management¶
Organization Users¶
Manage users and their access levels:
 Organization user list with roles and permissions
Organization user list with roles and permissions
User Information: - Name & Email: User identification - Role: Admin, User, Viewer - Last Login: Recent activity - Status: Active, Inactive, Pending
Role-Based Access Control¶
Available Roles: - Admin: Full organization management access - User: Create and manage own content - Viewer: Read-only access to shared content
Permission Matrix:
| Feature | Admin | User | Viewer |
|---|---|---|---|
| Data Builder | Full | Full | Read |
| Deployment Manager | Full | Own | Read |
| Organization Settings | Full | None | None |
| API Tokens | Full | Own | None |
| Trusted IPs | Full | None | Read |
| Audit Logs | Full | None | None |
Security Best Practices¶
Organization Security¶
Security Checklist: - [ ] Configure organization timezone correctly - [ ] Create dedicated API tokens for each integration - [ ] Set up trusted IP addresses for all access points - [ ] Regularly review audit logs for anomalies - [ ] Rotate API tokens every 90 days - [ ] Monitor user access and permissions - [ ] Implement least-privilege access principles
Network Security¶
IP Security Guidelines: - Use specific IP addresses instead of broad ranges when possible - Document all trusted IP entries with clear descriptions - Regularly audit and clean up unused IP entries - Monitor for access attempts from untrusted IPs - Consider VPN or proxy configurations
API Security¶
Token Management: - Generate unique tokens for each application/service - Store tokens securely (never in source code) - Implement token rotation schedules - Monitor token usage in audit logs - Immediately revoke tokens after security incidents
Troubleshooting¶
Common Issues¶
Access Denied from Trusted IP
Issue: User blocked despite being on trusted IP list
Solutions:
1. Check IP address format and CIDR notation
2. Verify user's actual IP (may be behind proxy/NAT)
3. Check trusted IP is active
4. Review audit logs for specific error details
API Token Not Working
Issue: API requests failing with authentication errors
Solutions:
1. Verify token is active and not expired
2. Check token is included in Authorization header
3. Confirm token has required permissions
4. Review API endpoint URL and format
IPv6 Access Issues
Issue: IPv6 addresses not working correctly
Solutions:
1. Verify IPv6 format (compressed notation)
2. Check CIDR ranges for IPv6
3. Confirm network supports IPv6
4. Test with IPv4 fallback
Getting Help¶
Support Resources: - Audit Logs: Check security events for specific errors - IP Validation: Use online tools to verify IP formats - Documentation: Review security configuration guides - Support: Contact administrator for access issues
Next Steps¶
Now that you understand Organization Settings:
- Set up your first data pipeline with proper security
- Configure IP-based security for enhanced protection
- Learn about API integrations using your tokens
- Review troubleshooting guide for common issues
Ready to build secure data pipelines? Continue to Your First Pipeline!